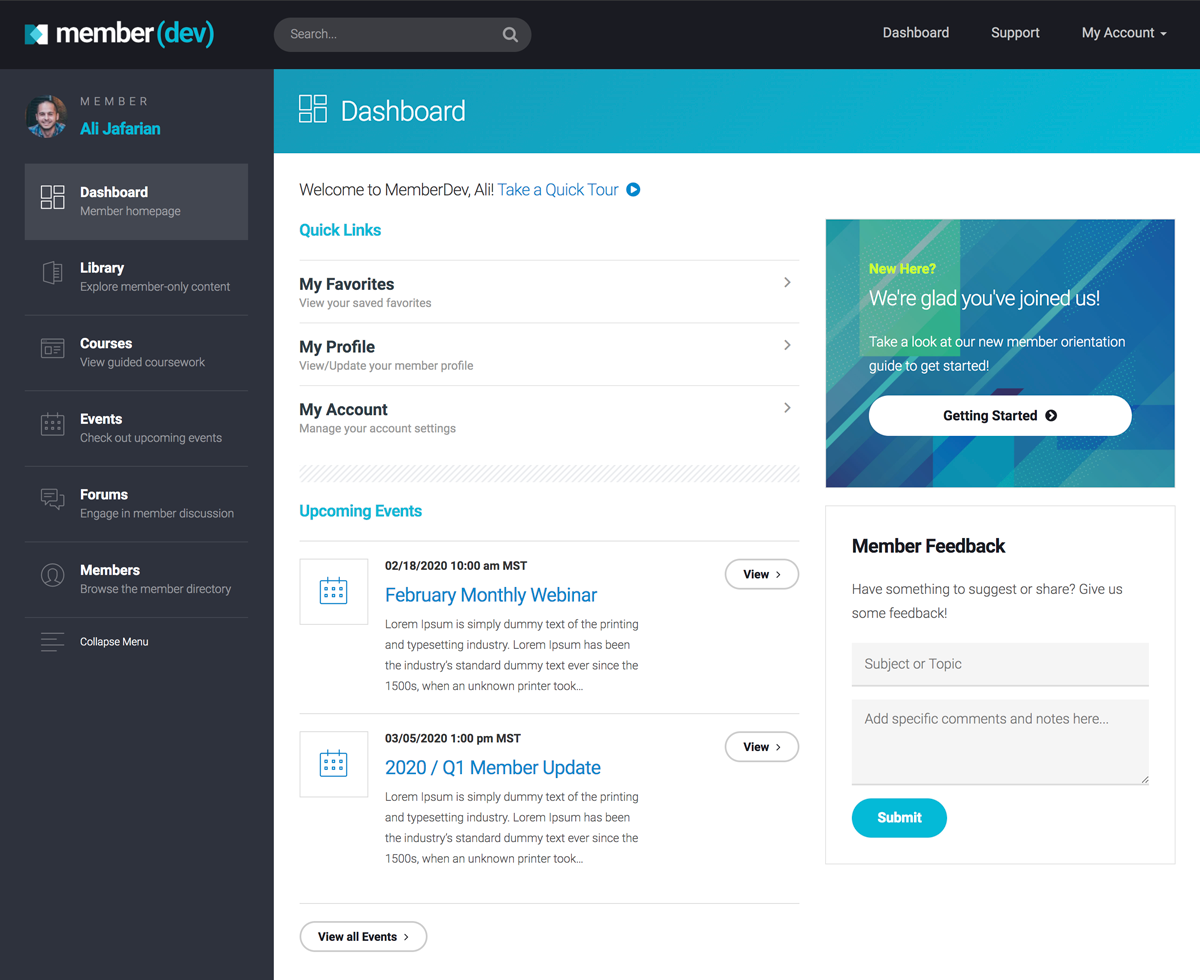
While we’d like to say that securing your WordPress membership site is as easy as installing a security plugin and calling it a day, there’s actually a lot that goes into protecting your online business.
Gone are the days when simple anti-spam or antivirus was enough. Modern cyberattacks can come from anywhere — “harmless” websites used as lures, software riddled with malware, themes and plugins loaded with built-in backdoors for hackers — with new threats appearing every year.
Even a seemingly “minor” attack can do irreparable damage. In fact, a hacker group was recently caught exploiting vulnerabilities in more than ten WordPress plugins to create rogue admin accounts in WordPress that could be used for monetary profit.
The reality is that your WordPress membership site is a gold mine for hackers, and in today’s threat landscape, the only way to properly protect your membership business is to understand the threats against you and to build a solid strategy for defense.
Why Membership Sites are a Target for Hackers
Whether you have ten members or thousands, your membership site is vulnerable to attack. In many cases, the smaller the business the greater the risk: over half of all cyberattacks hit small-to-medium (SMB) businesses. This is partly because many SMBs don’t see themselves as a target, and those that do often lack the budget to implement comprehensive security measures anyway.
Any site that collects and stores personal data like usernames, passwords, and credit card information is at high risk for data theft — including membership and subscription sites of all sizes.
Today’s cybercriminals aren’t just after your business, either. In addition to data theft, they may also attempt to breach your site in order to gain access to your partners’ or third-party suppliers’ sites instead — a network-based attack commonly known as “Island Hopping.”
Similarly, your membership site might be used for “watering hole” attacks, wherein hackers target frequently visited sites in an effort to steal credentials that can be used to hack other sites. Watering hole attacks are particularly harmful as they often can’t be detected without special tools.

To put this into perspective, if even one of your members uses the same password for Facebook as they do for your site, and Facebook gets hacked — the latest Facebook breach put 30 million users at risk, by the way — your site is automatically vulnerable.
Likewise, if your members use the same password for their bank accounts as they do for your site and your site gets breached, their personal finances are at risk — which is doubly bad news for you. Unfortunately, it only takes one breach to put you out of business or ruin your reputation with customers.
These types of cybersecurity gaps can be extremely difficult to fix if you don’t know they exist, which is why security awareness should be your number one priority.
The Top Cybersecurity Threats Against Your WordPress Site
So what type of threats do cybercriminals use to target your WordPress membership site? While “viruses” and “malware” may be the first things that come to mind, human-based threats are actually just as common.
Let’s look at some of the primary ways hackers attempt to breach your site.
Spear Phishing and Social Engineering
Spear-phishing is a targeted attempt to steal sensitive information using forms of personal communication, like email or text message. The most popular phishing trope is one you’ve likely heard before: a rich person from another country needs your help and will pay you handsomely, if only you loan them a little money first.
While these obvious scams still exist, modern phishing attacks have become much more complex and are often harder to distinguish.
Thanks to the rise of social engineering — where cybercriminals skim public social media profiles for sensitive information, like the name of your pet or the city you were born in — anyone can gain enough details about your life to send you a convincing message. It doesn’t help that 63% of all users keep their social media profiles open to the public.
Consider a scenario like this:
- A hacker finds the name of your freelance web developer from your company page.
- Posing as the owner of the company, they send an email with the subject line “Updated invoice for Q3.”
- A link in the email redirects to a password-protected internal document, which is actually a spoofed version of a traditional invoice.
- The marketer requests access to log in to view the document.
- The hacker now has their credentials and can gain access to your site.
Statistically speaking, 52% of all phishing attack victims will click a malicious link within an hour of receiving it. In fact, attacks like this are so effective that 91% of all cyberattacks start with a phishing email.
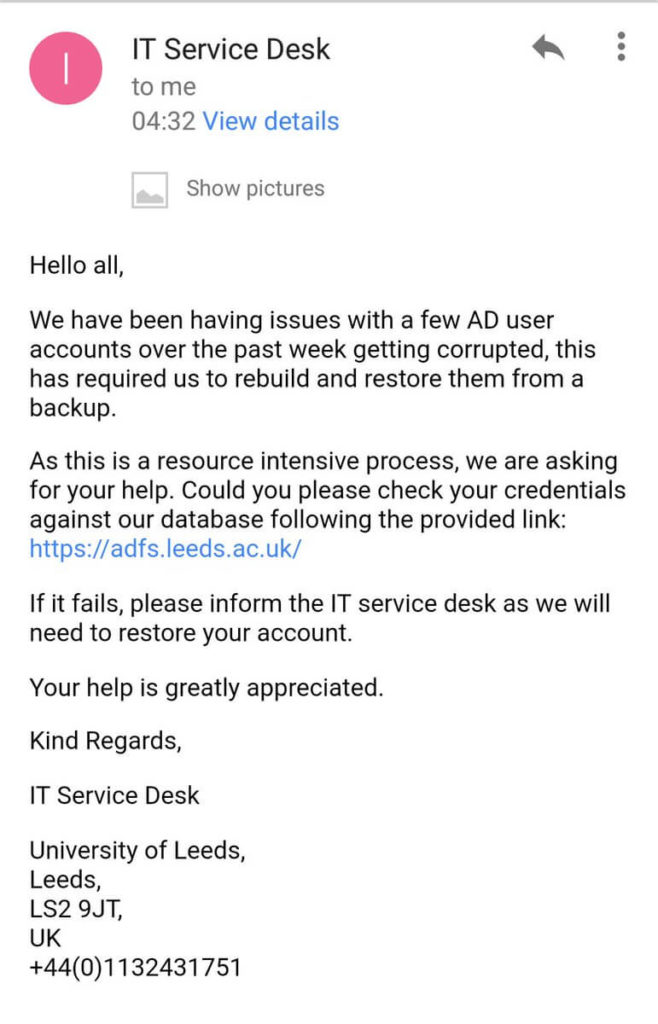
Another common scenario involves hackers mimicking the login of a site and sending phishing emails to users to “reset” their passwords. For membership sites that have gated members-only areas that contain sensitive data, that can be a big problem.
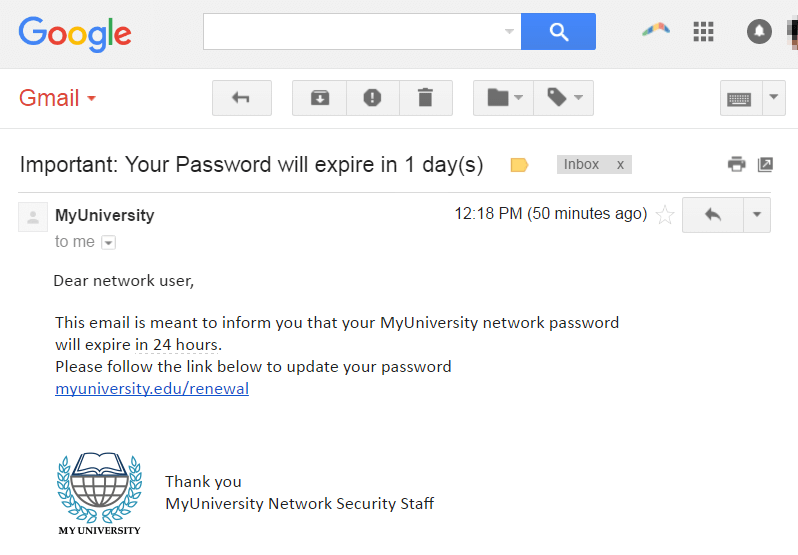
These types of phishing attacks work because they’re not suspicious — they come from known contacts, are written in casual language, and ask for things we do anyway, like click links or open documents. And all a hacker needs to do it successfully is an email address and some publicly available information.
Malware and Ransomware
Another primary concern for WordPress site owners is malware and ransomware, often hidden in third-party plugins. In fact, the Defiant Threat Intelligence team recently issued a warning for WordPress users of a “critical” hacking campaign in which malicious JavaScript is dropped on compromised web pages. When viewed by a WordPress admin, these pages trigger an AJAX call via jQuery that creates a rogue administrator account.
In short, malicious parties are able to create new users with admin privileges on a victim’s WordPress site with little to no warning.
After gaining access to the WordPress admin console, a hacker can exploit a WordPress site in any number of ways, from gathering financial information and other sensitive data about users and customers, or even uploading malicious files directly to a site’s main web directory.
BE WARNED: The threat actors behind the most recent campaign are leveraging third-party WordPress plugins to download the initial JavaScript.
A recent report by Imperva found that 98% of WordPress vulnerabilities are related to plugins.
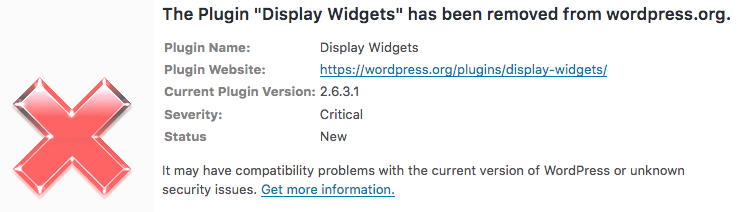
Plugins aren’t the only way your site can be compromised. Employees or even customers can create “backdoors” to your site by clicking malicious links on social media, often distributed via seemingly legitimate-looking ads, or other third-party sites.
According to new research from Bromium, Facebook, Twitter, Instagram, and other high-traffic social media sites are now “massive centers for malware distribution and other kinds of criminal activity.” The study also found that one in five businesses have been infected with malware distributed via a social media platform, and more than 12% already have experienced a data breach as a result.
Cryptojacking and Formjacking
Though somewhat on the decline, cryptojacking is still considered by many cybersecurity experts to be a major threat.
Cryptojacking is when hackers secretly use (or “hijack”) your computer to mine cryptocurrency. Similar to malware or ransomware, victims often unknowingly install a program on their computer that mines cryptocurrency in the background while normal applications run.
Another version of this threat — known as “in-browser” cryptojacking — doesn’t need a program to be installed, and instead uses JavaScript on a web page to mine for cryptocurrencies while the browser is active.
In 2018, nearly 50,000 sites were affected by cryptojacking, and at least 7,000+ of the compromised sites were powered by WordPress.
Of course, that number has decreased thanks in part to the shutdown of Coinhive, the largest cryptomining script engine used by hackers, in March of 2019.
The general plunge in the value of cryptocurrencies over the last few years has also contributed to its decline, but there are still other cryptomining services active that can be exploited, such as Cryptoloot, JSEcoin, and Deepminer. So while it’s (hopefully) on its way out, cryptojacking should still be considered a present threat.
WordPress users should also be wary of its “cousin,” known as formjacking, which is still alive and kicking. Formjacking is when cybercriminals load malicious code onto retailers’ websites to steal credit card details. It’s estimated that at least 4,800+ unique websites are compromised by formjacking every month.
How to Protect Your WordPress Site
So how do you protect your WordPress membership site from today’s biggest cybersecurity threats? Here are a few best practices to follow to ensure your site is secure:
- Practice security awareness
- Invest in third-party WordPress security
- Be smart about WordPress plugins
- Lockdown admin privileges
- Find back-end security gaps
- Move your WordPress site to SSL/HTTPS
1. Practice security awareness
First, keep up-to-date with the biggest threats and warnings around cybersecurity. The FBI and homeland security, as well as other dedicated news sites, regularly release alerts and activity monitoring for today’s top threats.
Here are a few cybersecurity news and alert sites to bookmark:
Second, make sure you, your employees or any team members (including freelancers), and your customers understand and follow cybersecurity best practices, including but not limited to:
- Creating strong, unique passwords for every site and never sharing or reusing passwords
- Protecting personal data online (not oversharing on social media, never giving out public details like your logins or passwords, answers to security questions, SSN, etc.)
- Avoiding clicking pop-ups or links, opening unknown emails or DMs, and downloading suspicious files
- Connecting to secure Wi-Fi with the use of a VPN if necessary
- Investing in security and establishing basic firewall and antivirus/anti-malware protection on every device
- Patching and keeping devices and software up-to-date
You can also participate in and offer regular security awareness training to your customers and employees/team members. The U.S. Department of Health and Humans Services offers free security awareness training and other cybersecurity resources.
2. Invest in third-party WordPress security
While WordPress does have some built-in security features, it can’t catch everything. Cybercrime is constantly evolving, and hackers are getting smarter and leveraging new technology every day. That’s why it’s worthwhile to consider investing in a paid third-party security solution that can monitor your site for current and new threats.
While free security solutions are available, they’re often not as robust as paid cybersecurity services and can lack some key features of proper services like continuous threat monitoring, remediation and disaster recovery, and access to expert advice and support.
At MemberDev, we recommend Sucuri Security as an affordable, scalable, and comprehensive cybersecurity solution for membership and subscription sites.
3. Be smart about WordPress plugins
Because WordPress plugins are a potential point-of-access for hackers, it’s imperative to ensure that your WordPress plugins are verified. This means choosing plugins that:
- Are compatible with the latest version of WordPress
- Are frequently updated
- WordPress has deemed safe
- Have strong user ratings
- Have easily accessible documentation
- Have a positive developer reputation
If you notice any of these signs, you may need to delete a plugin, as it could be a security risk. If you’re unsure about the safety of any of your WordPress plugins, you can always use a tool like WPScan (recommended by Sucuri Security) to verify your plugins before you download them.
For membership sites, in particular, which host sensitive information, like customer financial data and other credentials, you will need a membership plugin that has built-in security features.
That’s why we recommend MemberMouse, which is PCI-compliant to protect your member’s billing information and includes other security features, like auto-lock on shared accounts and password resets.
4. Lockdown admin privileges
WordPress admin privileges are a prime target for hackers, you want to ensure that your admin accounts are locked down. This means:
- Changing the default username from ‘admin’ to something unique (if you used a 1-click installer for WordPress)
- Creating strong, unique passwords for every admin account (if you allow freelancers or third-party partners to access your WordPress backend, ensure that they know how to create strong passwords)
- Regularly changing passwords for all accounts
- Password protect the admin directory (follow this guide from WPBeginner)
- Regularly checking your admin accounts to see that no new or suspicious accounts have been created.
Two additional action steps that can help secure your admin area from potential hackers including:
- Adding two-factor authentication through Google Authenticator
- Limiting login attempts with Login Lockdown.

5. Disable back-end security gaps
If you have some basic knowledge of code, there are a few other ways you can shore up security gaps in your WordPress website, such as:
- Disabling file editing
- Disabling PHP File Execution
- Adding Two Factor Authentication
- Changing WordPress Database Prefix
- Disabling Directory Indexing and Browsing
- Disabling XML-RPC in WordPress
- Automatically logging out Idle Users
- Adding Security Questions to WordPress Login
We’re not going to reinvent the wheel here, as WPBeginner has done a great job of outlining how to take these steps in their cybersecurity guide (found here).
While these steps may seem like “overkill,” it’s important to remember that the majority of cybercrime victims become victims because they don’t take the necessary steps to protect themselves. You’re never “too small” of a WordPress membership site to be a target.
6. Move your WordPress site to SSL/HTTPS
There are plenty of reasons to move your WordPress site to SSL/HTTPS if you haven’t already, including the fact that Google uses SSL as a ranking factor. If your membership site accepts payments of any kind, chances are high that you already have an HTTPS site. If not, it’s a good idea to invest in one, as SSL/HTTPS offers additional protection.
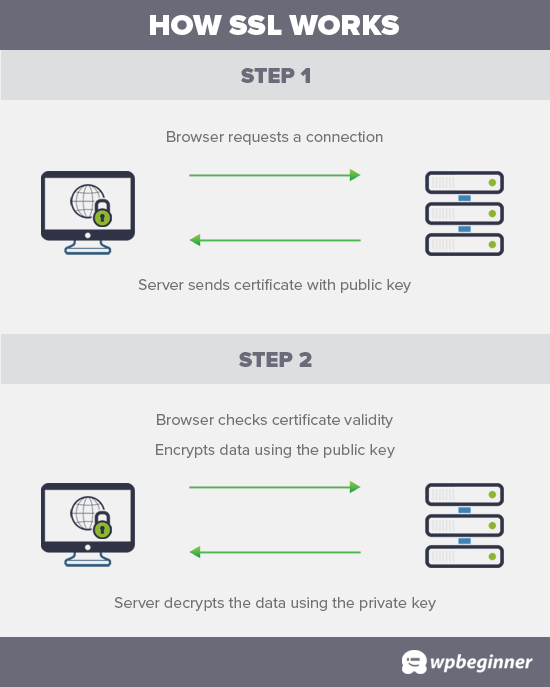
However, the reason this one is last on the list is that an SSL certificate alone cannot protect you against the majority of threats. In fact, many phishing sites now use SSL certificates and HTTPS to trick internet users into believing they are secure, legitimate pages.
But when used in combination with the above security measures, adding SSL/HTTPS can give you — and your customers — an added level of peace.
Cybersecurity Resources
Step-by-step WordPress security guides:
Other cybersecurity guides and training resources:
- How to Create Strong Passwords | Webroot
- How to Spot a Phishing Email | IT Governance
- How to Spot Malware | CSO Online
- How to Tell If You’ve Been Crytojacked | CloudTweaks
- How to Tell If Your WordPress Site Has Been Hacked | WordFence
- Cryptojacking (Browser) Test Tool | Opera
- WordPress Website Hacking Remediation | WP Buffs
- Security Awareness Training for IT Professionals | Infosec Institute
Cybersecurity news and alert sites:

Joanne Penn
Joanne is a content strategist at MemberDev. She helps B2B and SaaS companies promote their message and drive engagement through well-researched content marketing.